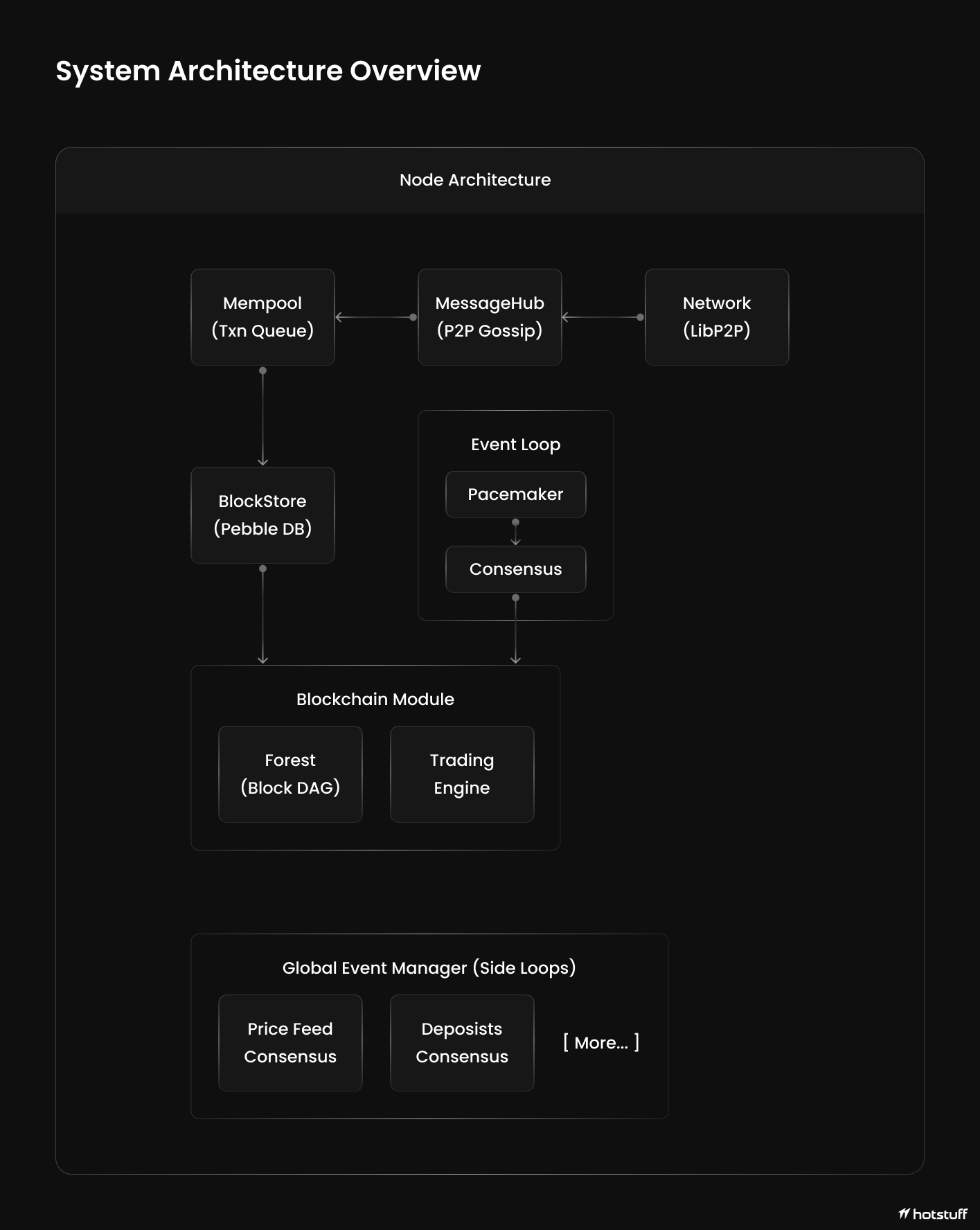
System Model
The protocol operates under the partially synchronous network model:- n = 3f + 1 validators, tolerating up to f Byzantine faults.
- Partial Synchrony: After GST, message delivery bounded by a known constant.
- Authenticated Channels: All messages signed with digital signatures.
- Collision-Resistant Hashing: SHA256 for state commitments.
Two-Chain Finality
A block B at view v is finalized when a child block B’ at view v+1 contains a QC for B. Finality time: 2 rounds (versus 3 rounds for standard HotStuff).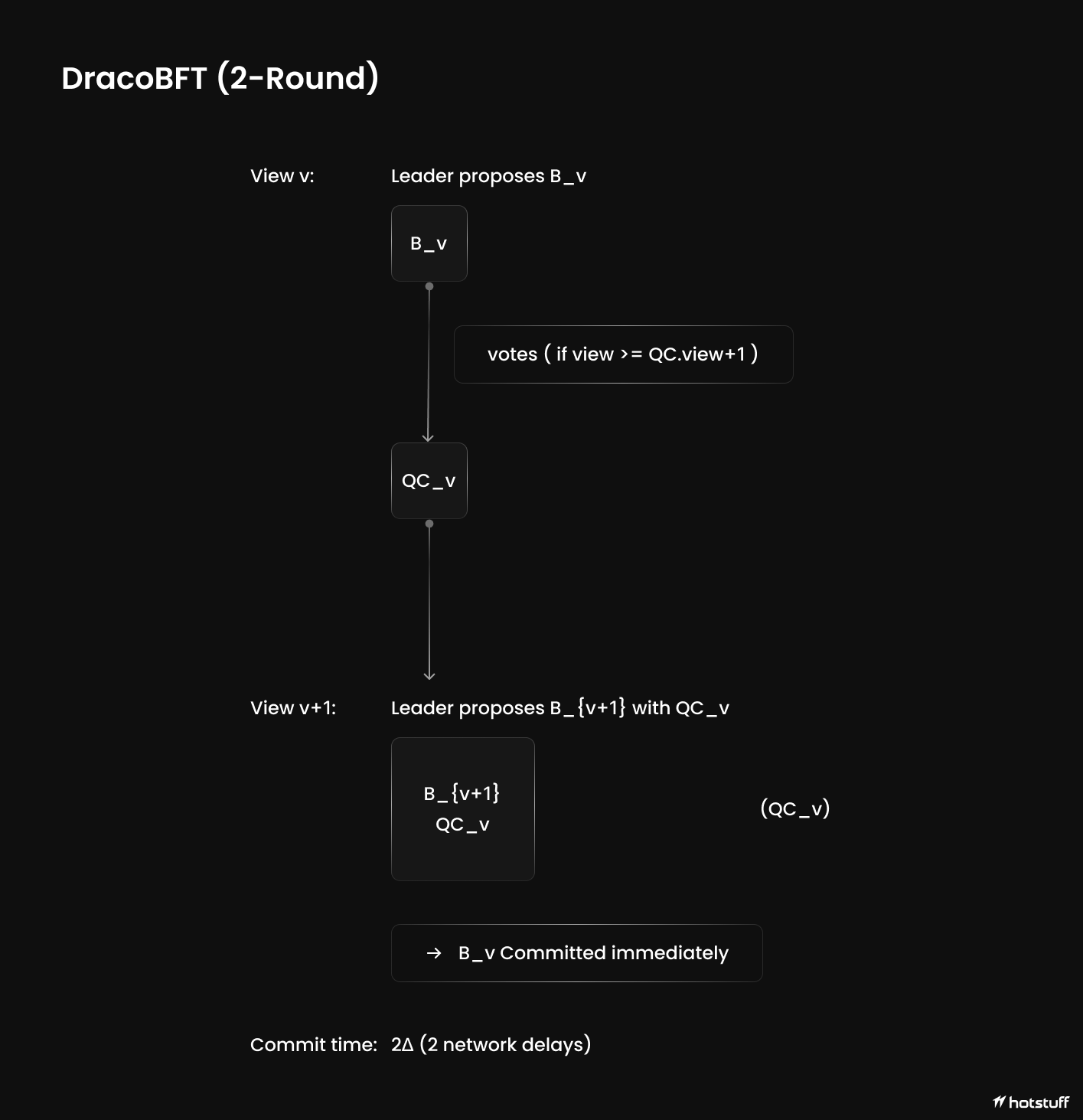
Vote Rule
Validators only vote for blocks that directly extend a certified block:Change-Log Hash (CLH)
Instead of computing global state roots, DracoBFT commits only to state modifications.The State Root Performance Problem
Traditional Merkle Patricia Tries incur O(n log n) costs for global state updates. The bottleneck is disk I/O, not computation. For a binary MPT with billions of keys, this translates to dozens of random disk reads per state update. Recent analysis shows that state root computation can cause up to 10x slowdown in block building.DracoBFT Approach
DracoBFT replaces state root computation with Change-Log Hashes computed during block execution. Rather than committing to the entire state, CLH commits only to state modifications.Block-Level Aggregation
If 400 transactions modify the same key, CLH hashes it once (final value), not 400 times.| System | Hash Operations (400 txns, 1 key) |
|---|---|
| Ethereum MPT | ~4,000 |
| Tendermint IAVL | ~2,000 |
| Naive CLH | 400 |
| DracoBFT CLH | 1 |
Chained CLH
Auxiliary Verification Loops
DracoBFT processes external operations in parallel with consensus through a modular global event management system.
Phase 1: Proof Collection
Collect external action proofs (zkTLS or ZK execution).Phase 2: Verification
Verify proofs using appropriate verifier, generate verification certificate.Phase 3: Consensus Integration
Package verified action as transaction, submit to mempool.Phase 4: Finalization
On block finalization, apply state transition atomically.Trustless Verification Architecture
zkTLS for Off-Chain Data
For public or private API calls to external services, DracoBFT leverages zero-knowledge Transport Layer Security (zkTLS) proofs. These proofs provide cryptographic verification of HTTPS responses without requiring the external service to be aware of the blockchain. Validators can verify:- The response came from the claimed server (via TLS certificate chain).
- The response content matches specific claims (via ZK proof).
- The data was not tampered with (via server signature).
ZK Execution Proofs for On-Chain State
For verification of state or events on other blockchains (for example, Ethereum):- zkTLS-based RPC proofs: Efficient verification (under 100ms generation, under 10ms verification) with RPC provider trust.
- Zero-knowledge execution proofs: Full trustlessness via recursive block header and state verification.
Validator-as-Service-Provider Model
Beyond traditional block validation, the auxiliary verification architecture enables validators to function as permissioned access points to external services.Routing Mechanism
The system matches end-users to specific validators based on:- Validator stake (economic security collateral).
- Historical performance and uptime metrics.
- Geographic proximity and regional service coverage.
- Quality-of-service parameters (latency, availability).
- Supported service integrations (payment rails, fiat currencies, banking partners).
Regulatory Compliance
The validator-as-service architecture accommodates regulatory diversity through geographic validator distribution and selective service provision. Validators opt in to specific services based on their regulatory compliance capabilities.View-Change Protocol
Linear complexity O(n) view change:Weighted Leader Selection
Deterministic weighted random selection with epoch-based computation:- Proportional probability: Stake s gives probability s/totalStake.
- Determinism: All validators compute identical schedule.
- Efficiency: O(n) per epoch.
- Dynamic updates: Recomputed on validator set changes.
Protocol Comparison
| Protocol | Optimistic Path | View-Change | State Commitment |
|---|---|---|---|
| PBFT | 3 rounds | O(n^2) msgs | O(n) |
| HotStuff | 3 rounds | O(n) msgs | O(n log n) |
| Tendermint | 3 rounds | O(n^2) msgs | O(n log n) |
| DracoBFT | 2 rounds | O(n) msgs | O(m) |
Use Cases
Trustless Bridges
Verify deposit events on external blockchains without trusted relayers or multisig committees. ZK execution proofs provide cryptographic verification of deposit transactions.Verifiable Oracle Feeds
Obtain price data, identity verification, or real-world events from traditional APIs with zkTLS proofs. Validators verify cryptographic proofs rather than trusting oracle providers.Financial Service Access
Validators provide permissioned access to payment processors, banking APIs, foreign exchange platforms, and card issuance services. zkTLS proofs verify service delivery including payment authorization responses within required latency windows (under 300ms for card transactions).Cross-Chain State Queries
Access state from external blockchains (token balances, contract storage, historical events) with cryptographic verification, enabling DeFi applications that span multiple chains.Architecture Summary
| Component | Complexity | Benefit |
|---|---|---|
| Consensus | O(n) | Linear message complexity. |
| View Change | O(n) | No quadratic bottleneck. |
| State Commitment | O(m) | Eliminates trie I/O. |
| Finality | 2 rounds | Sub-second confirmation. |